 For several years, the combination of system integration, the smart grid and the legacy of outdated industrial control systems have been presenting new cyber security challenges for energy infrastructures. These problems are reflected in the 10 most common anomalies identified in energy companies' operational technology (OT) networks in 2022.
For several years, the combination of system integration, the smart grid and the legacy of outdated industrial control systems have been presenting new cyber security challenges for energy infrastructures. These problems are reflected in the 10 most common anomalies identified in energy companies' operational technology (OT) networks in 2022.
Digitalization and pan-European system integration represent a double-edged sword for energy companies. On the one hand, they will simplify processes and cross-border collaboration, while also making new business models possible. On the other hand, increasing networking, the integration of operational technology (OT) into IT and the expansion of the smart grid are exposing the already very vulnerable critical infrastructure to a higher level of risk.
The smart grid in particular offers attackers millions of potential access points, such as publicly accessible smart meters, charging stations and energy storage systems. The situation is made more difficult by the unique features of OT. Its focus is on process stability, availability and occupational safety, rather than information security. As a result, very few industrial components are designed to provide additional security functions. As a general rule, they are insecure by design. In the past, cyber security was not an issue in OT, which originally consisted of isolated systems that were only accessible to the company's own engineers.
No industrial control system is secure
These characteristics are also reflected in the results of almost two dozen Rhebo Industrial Security Assessments (RISSA) which were carried out in 2022, primarily among German energy companies (Fig. 1). During a RISSA, the OT infrastructure and communications are investigated specifically with the aim of identifying risks, anomalies and security threats. On average 18 types of anomalies were identified in each risk analysis. Individual anomalies were found several times in one single RISSA, but were not counted separately in the assessment. Instead they were grouped into anomaly types. This means that the absolute number of anomalies identified in the OT networks is generally much larger than the aggregated average value.
It is noticeable that the majority of the risks and anomalies relate to legacy problems:
- Legacy protocols: In 86.4 percent of all risk analyses, communication using historic protocol types was identified. These protocols do not allow for any kind of authentication or encryption. This enables intruders to extract information from the infrastructure which will be valuable to them during the subsequent phases of an attack.
- Obsolete protocols: In 82 percent of all cases, protocols were being used that were not relevant to the OT infrastructure in question. Frequently this involved multicast messages that devices use by default to advertise their own services and software versions. Unneeded protocols represent potential attack vectors and should therefore be removed.
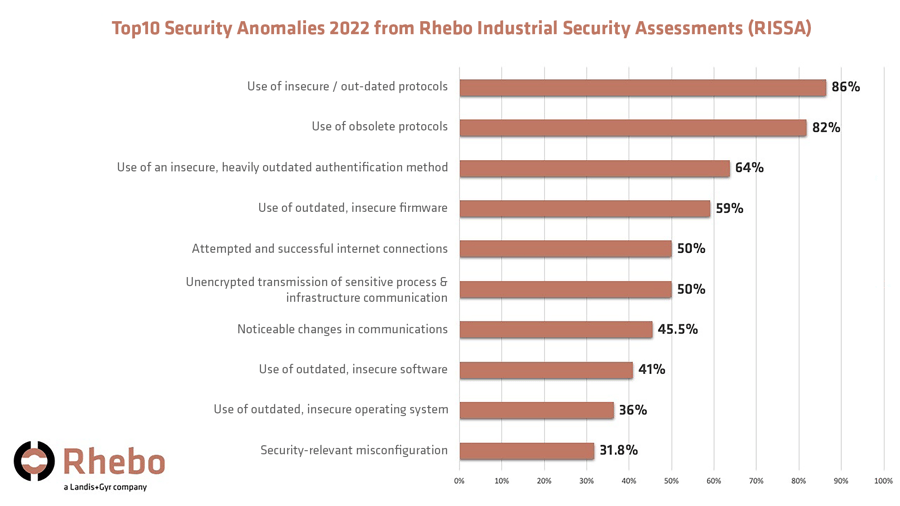
Fig. 1: Top 10 security anomalies identified in 2022 in Rhebo InduStrial Security Assessments. The figures show the number of analyses where each anomaly was found. (Source: Rhebo)
- Outdated authentication method: In 64 percent of all cases, an authentication method was found that had not been supported by the vendor for more than ten years. For several years, it has been possible to decrypt its password hashes using graphics cards in just six hours. The use of this method has also been responsible for many zero-day vulnerabilities in this vendor's systems in recent years.
- Unencrypted transmission of sensitive infrastructure information: In 50 percent of all cases, communication with plain text passwords was found. For attackers with access to the OT network, this vulnerability is a valuable source of information for lateral movement and threat propagation.
- Vulnerable firmware, software or operating system: Almost all the OT networks included systems and devices that have had known vulnerabilities for some time and that have not yet been patched or replaced by the operator. Outdated firmware on network components in particular represents a widespread problem
- Security-relevant misconfigurations: In one third of all the risk analyses, misconfigurations were detected that would enable intruders to obtain sensitive information or launch man-in-the-middle attacks. The misconfigurations that were identified included configuration via DHCP both in the network and in components searching for a corresponding server, as well as router advertisements and source routing.
Generally, attackers can only exploit these risks if they already have access to the network. Nevertheless, they form a valuable arsenal that allows attackers to move laterally in the network, to understand the infrastructure and to consolidate and extend their access to critical infrastructure.
There are also anomalies that pose risks for process security but are hidden from operators because of their lack of visibility in the OT:
- Establishing a connection to the internet: In half of all cases, there were devices that established or tried to establish connections to public IP addresses. Often these were DNS queries that bypassed the system's own DNS server. However, there were also systems that obtained their updates from the internet without administrative checks. In many cases, the attempts were blocked by local firewalls, but there were not always rules in place to prevent these connection attempts. Successful connections to external networks not only represent an information leak from the company's network. They can also indicate existing intrusion activities
- Noticeable changes in communications: In 46 percent of all cases, unexpected changes took place in OT communications. Industrial communication is characterized by repetitive and deterministic patterns. Sudden crashes, peaks or even a change in traffic patterns can be indications of active interventions in the behavior of a system or a device.
Methodology: From black box to visibility
To run the risk analysis, an OT monitoring system with anomaly detection functions was integrated into neuralgic points in the OT. The system is generally installed via switch ports that mirror the traffic. The installation is completed in just a few minutes without affecting the OT itself. After this, the communication in the OT is recorded passively over an average period of 14 days. This recording forms the basis for the detailed evaluation by OT experts which produced the results outlined above. In addition to creating a list of all anomalies and risks, they identify and document all the active systems and devices, as well as their connections and the quality of these connections (Fig. 2).
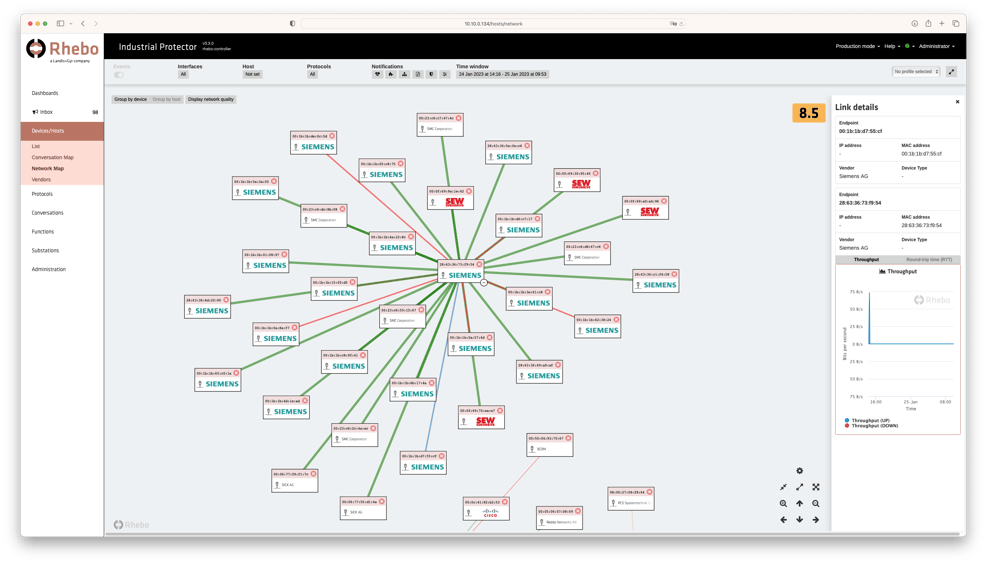 Fig. 2: The OT monitoring system visualizes the entire monitored operational technology and shows all the systems, their connections and properties. (Source: Rhebo)
Fig. 2: The OT monitoring system visualizes the entire monitored operational technology and shows all the systems, their connections and properties. (Source: Rhebo)
Typically, the OT monitoring and anomaly detection system remains in the OT after the risk analysis has been completed and is directly set to continuous operation. The OT communication that has been streamlined on the basis of the risk analysis is used as the baseline for the detection of future anomalies. In IEC 61850 infrastructures, the .scd file can also be imported. Anomalies that were identified during the risk analysis, but have not yet been resolved, can be given "Monitor" status in the OT monitoring system. This allows managers to track them and monitor their frequency until a solution is found.
The OT monitoring system with anomaly detection allows all communications to be continuously monitored during ongoing operations and security anomalies to be identified in real time. As a result, energy supply companies can meet the requirements of the German Federal Office for Information Security (BSI) laid down in its orientation guide for the "Operation of Intrusion Detection Systems."






