 The utility industry is facing new and evolving security threats in the modern era of operational technology (OT) and information technology (IT) convergence. Geopolitical turmoil and changes in the workforce have further complicated the security landscape for utilities. As a result, it is becoming increasingly important to secure advanced metering infrastructure (AMI) systems.
The utility industry is facing new and evolving security threats in the modern era of operational technology (OT) and information technology (IT) convergence. Geopolitical turmoil and changes in the workforce have further complicated the security landscape for utilities. As a result, it is becoming increasingly important to secure advanced metering infrastructure (AMI) systems.
In the past, cyber security was not an issue in operational technologies (OT), which consisted of isolated systems that were only accessible to the company's own engineers and sometimes remote access by service contractors. Today however, with the convergence of OT and ICT and the extension of operational networks to the IoT edge, the smart grid provides attackers millions of potential access points, including publicly accessible smart meters, charging stations and energy storage systems. The traditional focus of OT systems on process stability, availability and occupational safety often leaves information security unaddressed. Historically, few industrial components are designed to provide any cybersecurity function and vendors are only slowly progressing towards security-by-design principles well know from traditional IT.
An expanded threat surface
While digitalization and pan-European system integrations have simplified processes, improved cross-border collaboration and ushered in new business models possible, they have also exposed critical infrastructure to an expanded threat surface that comes with the OT-IT convergence. Some of the challenges from this are reflected in Rhebo's report on 10 most common anomalies identified in energy companies' operational technology (OT) networks in 2022. 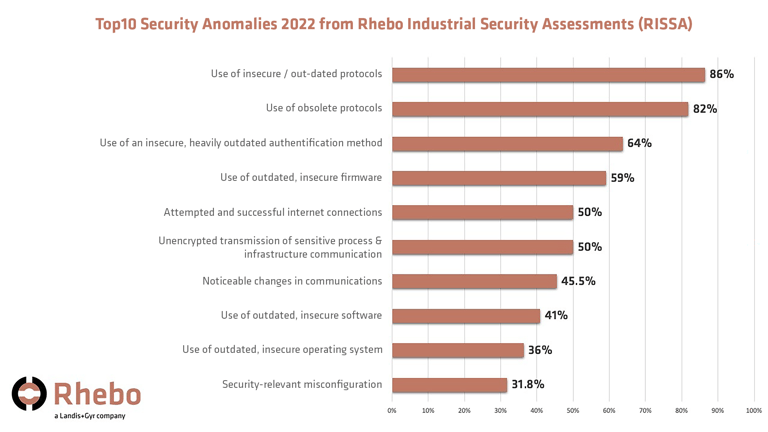
Additionally, geopolitical tensions and shifting workforce dynamics can increase the risk of insider threats as well as multi-stage cyberattacks that can include zero-day exploits overlooked by common perimeter security tools and supply chain compromise via third-party components and cloud-based systems.
End to end approach
Securing AMI systems requires a multi-layered, end-to-end, defense-in-depth approach with thorough risk assessment that addresses all key components of the infrastructure, including endpoints, network, data centers, software, third-party components, and cloud.
- Smart meters and communication devices: The endpoints, such as meters and communication devices, must be secured against tampering and hacking.
- The network: It must be protected against cyberattacks, such as denial of service attacks, eavesdropping, and data tampering. The data centers must be secured against cyberattacks, as well as physical attacks.
- Software and applications: The software used to manage and process AMI data must be secure, and strong authentication and authorization controls must be in place to ensure that only authorized users can access sensitive information. Secure software development lifecycle (S-SDLC) improves the so-called shift-left of security i.e. conducting security testing sooner in the development cycle.
- Third-party components: Third-party components, including communication devices, meter reading software, and analytics tools, must be properly secured to prevent the introduction of malicious software or hardware. Future SBOM requirements address this challenge by increasing transparency along the supply chain. Where security can not be fully accomplished (i.e. due to capacity or in process-critical legacy systems), the continuous monitoring of these devices helps to detect security breaches and to prevent threat propagation.
- Vulnerability management: Today software often consists of other 3rd party components, and bugs and vulnerabilities are a reality faced by everyone. Effective vulnerability management helps to triage and prioritize by taking into account the real and current threats in the industry.
- Identity and access management: Controlling the access to an AMI system must be governed by effective policies and technical means to ensure minimized risk from internal attacks. RBAC and fine grained permission are today already employed to smart meters by using different meter clients for well-defined actions.
- Defence-in-depth: There is no 100 % security – more often then not, attackers are one step ahead of the game. They have time on their side and must only find one weakness while defenders must guard all. Therefore, the concept of defence-in-depth needs to be followed establishing multiple layers of security throughout the AMI solution. Each additional layer increases the cost for an effective attack thus preventing successful compromise and disruption. One example is the combination of classic perimeter security (i.e. firewalls) and a network-based monitoring with anomaly detection. If a firewall fails to block a professional attack (for example via zero-day exploits or hijacked user credentials), the monitoring with anomaly detection will detect the attack via behavioral analysis early on.
- Grid Resilience: Defence-in-depth can also be applied to grid edge components themselves. Failing controls and devices can be contained by continuously monitoring the network communications of the AMI without requiring changes to the AMI architecture or devices. Effective monitoring can ensure that cascading faults and threat propagation are minimized and contained.



.jpeg?width=120&height=120&name=Anoop_Gangadharan%20(1).jpeg)



